|
|

iOS 9 running on an iPhone 6S
|
|
| Developer | Apple Inc. |
|---|---|
| Written in | C, C++, Objective-C, Swift |
| OS family | Unix-like, based onDarwin (BSD), OS X |
| Working state | Current |
| Source model | Closed source |
| Initial release | June 29, 2007 |
| Latest release |
9.2.1 (13D20) (February 18, 2016[1]) [±]
7.2 (12F69) (April 8, 2015[2]) [±]
|
| Latest preview | 9.3 Beta 3 (13E5200d)(February 8, 2016) [±] |
| Marketing target | Smartphones, tablet computers |
| Available in | 40 languages[4][5][6][7] |
| Update method | iTunes or OTA (iOS 5 or later) |
| Platforms |
Discontinued:
|
| Kernel type | Hybrid (XNU) |
| Default user interface | Cocoa Touch (multi-touch, GUI) |
| License | Proprietary softwareexcept for open-source components |
| Official website | www.apple.com/ios/ |
iOS (originally iPhone OS) is a mobile operating system created and developed by Apple Inc. and distributed exclusively for Apple hardware. It is the operating system that presently powers many of the company’s mobile devices, including the iPhone, iPad, andiPod touch. It is the second most popular mobile operating system platform in the world by sales, after Android.
Originally unveiled in 2007, for the iPhone, it has been extended to support other Apple devices such as the iPod Touch(September 2007), iPad (January 2010), iPad Mini (November 2012) and second-generation Apple TV onward (September 2010). As of January 2015, Apple’s App Store contained more than 1.4 million iOS applications, 725,000 of which are native for iPads.[8]These mobile apps have collectively been downloaded more than 100 billion times.[9]
The iOS user interface is based on the concept of direct manipulation, using multi-touch gestures. Interface control elements consist of sliders, switches, and buttons. Interaction with the OS includes gestures such as swipe, tap, pinch, and reverse pinch, all of which have specific definitions within the context of the iOS operating system and its multi-touch interface. Internalaccelerometers are used by some applications to respond to shaking the device (one common result is the undo command) or rotating it in three dimensions (one common result is switching from portrait to landscape mode).
iOS shares with OS X some frameworks such as Core Foundation and Foundation Kit; however, its UI toolkit is Cocoa Touch rather than OS X’s Cocoa, so that it provides the UIKit framework rather than the AppKit framework. It is therefore not compatible with OS X for applications. Also while iOS also shares the Darwin foundation with OS X, Unix-like shell access is not available for users and restricted for apps, making iOS not fully Unix-compatible either.
Major versions of iOS are released annually. The current release, iOS 9.2, was released on December 8, 2015. In iOS, there are four abstraction layers: the Core OS layer, the Core Services layer, the Media layer, and the Cocoa Touch layer. The current version of the operating system (iOS 9), dedicates around 1.3 GB of the device’s flash memory for iOS itself.[10] It runs on theiPhone 4S and later, iPad 2 and later, iPad Pro, all models of the iPad Mini, and the 5th-generation iPod Touch and later.
History
In 2005, when Steve Jobs began planning the iPhone, he had a choice to either “shrink the Mac, which would be an epic feat of engineering, or enlarge the iPod”. Jobs favored the former approach but pitted the Macintosh and iPod teams, led by Scott Forstalland Tony Fadell, respectively, against each other in an internal competition, with Forstall winning by creating the iPhone OS. The decision enabled the success of the iPhone as a platform for third-party developers: using a well-known desktop operating system as its basis allowed the many third-party Mac developers to write software for the iPhone with minimal retraining.[11] Forstall was also responsible for creating a software developer’s kit for programmers to build iPhone apps, as well as an App Store withiniTunes.[12][13]
The operating system was unveiled with the iPhone at the Macworld Conference & Expo, January 9, 2007, and released in June of that year.[14] At first, Apple marketing literature did not specify a separate name for the operating system, stating simply what Steve Jobs claimed: “iPhone runs OS X” and runs “desktop applications”[15][16] when in fact it runs a variant of [Mac] OS X, that doesn’t run OS X software unless it has been ported to the incompatible operating system. Initially, third-party applications were not supported. Steve Jobs’ reasoning was that developers could build web applications that “would behave like native apps on the iPhone”.[17][18]On October 17, 2007, Apple announced that a native Software Development Kit (SDK) was under development and that they planned to put it “in developers’ hands in February”.[19] On March 6, 2008, Apple released the first beta, along with a new name for the operating system: “iPhone OS”.
On September 5, 2007, Apple released the iPod Touch, which had most of the non-phone capabilities of the iPhone. Apple also sold more than one million iPhones during the 2007 holiday season.[20] On January 27, 2010, Apple announced the iPad, featuring a larger screen than the iPhone and iPod Touch, and designed for web browsing, media consumption, and reading iBooks.[21]
In June 2010, Apple rebranded iPhone OS as “iOS”. The trademark “IOS” had been used by Cisco for over a decade for its operating system, IOS, used on its routers. To avoid any potential lawsuit, Apple licensed the “IOS” trademark from Cisco.[22]
By late 2011, iOS accounted for 60% of the market share for smartphones and tablets.[23] By the end of 2014, iOS accounted for 14.8% of the smartphone market[24] and 27.6% of the tablet and two-in-one market.[25] As of February 2015, StatCounter reported iOS was used on 23.18% of smartphones and 66.25% of tablets worldwide.[26]
Software updates
Apple provides major updates to the iOS operating system approximately once a year via iTunes and also, for devices that came with iOS version 5.0 or later, over the air. The latest version is iOS 9, which is available for the iPhone 4S, iPhone 5, iPhone 5C, iPhone 5S, iPhone 6, iPhone 6 Plus, iPhone 6S, iPhone 6S Plus, iPad 2, the third and fourth generation iPad, the first and second generation iPad Air, the iPad Pro, the first, second, third and fourth generation iPad Mini, and the fifth and sixth generation iPod Touch. The OS update was released on September 16, 2015.
Before the iOS 4 release in 2010, iPod Touch users had to pay for system software updates. Apple claimed that this was the case because the iPod Touch was not a ‘subscription device’ like the iPhone (i.e., it was a one-off purchase).[27] Apple said it had ‘found a way’ to deliver software updates for free to iPod Touch users at WWDC 2010 when iOS 4 was unveiled.[28]
Features
Home screen
The home screen (rendered by and also known as “SpringBoard“) displays application icons and a dock at the bottom of the screen where users can pin their most frequently used apps. The home screen appears whenever the user unlocks the device or presses the “Home” button (a physical button on the device) whilst in another app.[29] Before iOS 4 on the iPhone 3GS and newer, the screen’s background could be customized with other customizations available through jailbreaking, but can now be changed out-of-the-box. The screen has a status bar across the top to display data, such as time, battery level, and signal strength. The rest of the screen is devoted to the current application. When a passcode is set and a user switches on the device, the passcode must be entered at the Lock Screen before access to the Home Screen is granted.[30]
In iPhone OS 3.0, the Spotlight feature was introduced. It allows users to search media, apps, emails, contacts, messages, reminders, calendar events, and similar content. In iOS 7 and later, Spotlight is accessed by pulling down anywhere on the home screen (except for the top and bottom edges that open Notification Center and Control Center).[31][32] In iOS 9, there are two ways to access Spotlight. As with iOS 7 and 8, pulling down on any homescreen will show Spotlight. However, it can also be accessed as it was in iOS 3 – 6. This gives a Spotlight endowed with Siri suggestions, which include app suggestions, contact suggestions and news.[33]
Since iOS 3.2, users are able to set a background image for the Home screen. This feature is only available on third-generation devices or newer – iPhone 3GS or newer, iPod Touch 3rd generation or newer (iOS 4.0 or later), and all iPad models (iOS 3.2 or later).
Researchers found that users organize icons on their homescreens based on usage-frequency and relatedness of the applications, as well as for reasons of usability and aesthetics.[34]
System font
iOS originally used Helvetica as the system font. With the release of the iPhone 4 and iOS 4, iOS used Helvetica Neue as the system font on devices with Retina Displays, but retained Helvetica as the system font for older devices.[35] iOS 7 provided the ability to scale text in apps or switch to Helvetica Neue Bold as the default system font, as accessibility options. iOS 9 changed the system font to San Francisco, a typeface designed by Apple for maximum legibility on computer and mobile displays, originally introduced as the system font for the Apple Watch.[36]
Folders
With iOS 4 came the introduction of a simple folder system. When applications are in “jiggle mode”, any two (with the exception of Newsstand in iOS 5 and iOS 6, which acts like a folder[37]) can be dragged on top of each other to create a folder, and from then on, more apps can be added to the folder using the same procedure, up to 12 on iPhone 4S and earlier and iPod Touch, 16 on iPhone 5, and 20 on iPad. A title for the folder is automatically selected by the category of applications inside, but the name can also be edited by the user. When apps inside folders receive badges, the numbers shown by the badges is added up and shown on the folder. Folders cannot be put into other folders, though an unofficial workaround exists that enables folders to be nested within folders.[38] iOS 7 updated the folders with pages like on the SpringBoard. Each page can hold nine apps, and the Newsstand app is now able to be placed into a folder.
Notification Center
Before iOS 5, notifications were delivered in a modal dialog box and could not be viewed after being dismissed. In iOS 5, Apple introduced Notification Center, which allows users to view a history of notifications. The user can tap a notification to open its corresponding app, or clear it.[39] Notifications are now delivered in banners that appear briefly at the top of the screen. If a user taps a received notification, the application that sent the notification will be opened. Users can also choose to view notifications in modal alert windows by adjusting the application’s notification settings. Introduced with iOS 8, widgets are now accessible through the Notification Center, defined by 3rd parties.
When an app sends a notification while closed, a red badge appears on its icon. This badge tells the user, at a glance, how many notifications that app has sent. Opening the app clears the badge.
Accessibility
Located in Settings > General > Accessibility. This allows the user to customize various aspects of the iPhone to assist the user if assistance is needed in the area of seeing or hearing. As well as the addition of accessibility shortcuts.[40]
Included applications
The iOS home screen contains these default “apps”. Some of these applications are hidden by default and accessed by the user through the Settings app or another method—for instance, Nike+iPod is activated through the Settings app. Many of these apps, such as Safari, the App Store, and Siri, can also be disabled in the Restrictions section of the Settings app.[41]
Each table’s green area below shows the iOS version for which each Apple model app feature first became available.
| Series | iPhone | iPod Touch | iPad | iPad Mini | |||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Model | 1st | 3G | 3GS | 4 | 4S | 5 | 5C | 5S | 6 | 6 Plus | 6S | 6S Plus | 1st | 2nd | 3rd | 4th | 5th | 6th | 1st | 2 | 3rd | 4th | Air | Air 2 | 1st | 2 | 3 | ||||||||
| Phone | Telephone | 1.0 | 2.0 | 3.0 | 4.0 | 5.0 | 6.0 | 7.0 | 8.0 | 9.0 | N/A | N/A | N/A | ||||||||||||||||||||||
| Email client | 1.1.3 | 2.1.1 | 3.1.1 | 4.1 | 6.0 | 8.4 | 3.2 | 4.2.1 | 5.1 | 6.0 | 7.0.3 | 8.1 | 6.0 | 7.0.3 | 8.1 | ||||||||||||||||||||
| Safari | Web browser | 1.1 | |||||||||||||||||||||||||||||||||
| Music | Portable media player | N/A | 5.0 | 5.0 | |||||||||||||||||||||||||||||||
| Videos | Video player | 3.2 | 4.2.1 | ||||||||||||||||||||||||||||||||
| SpringBoard | Home screen | 1.0 | 2.0 | 3.0 | 4.0 | ||||||||||||||||||||||||||||||
| Spotlightsearch | 3.0 | 3.0 | |||||||||||||||||||||||||||||||||
| Folders | N/A | 4.0 | N/A | 4.0 | 4.2.1 | ||||||||||||||||||||||||||||||
| Home screen backgrounds | N/A | 4.0 | N/A | 4.0 | 3.2 | ||||||||||||||||||||||||||||||
| Series | iPhone | iPod Touch | iPad | iPad Mini | |||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Model | 1st | 3G | 3GS | 4 | 4S | 5 | 5C | 5S | 6 | 6 Plus | 1st | 2nd | 3rd | 4th | 5th | 6th | 1st | 2 | 3rd | 4th | Air | Air 2 | 1st | 2 | 3 | ||||
| Messages | Text messaging | 1.0 | 2.0 | 3.0 | 4.0 | 5.0 | 6.0 | 7.0 | 8.0 | N/A | N/A | N/A | |||||||||||||||||
| MMS | N/A | 3.0 | |||||||||||||||||||||||||||
| iMessageinstant messaging | N/A | 5.0 | N/A | 5.0 | 6.0 | 5.0 | 5.1 | 6.0 | 7.0.3 | 8.1 | 6.0 | 7.0.3 | 8.1 | ||||||||||||||||
| Calendar | Calendar | 1.0 | 2.0 | 3.0 | 4.0 | 1.1 | 2.1.1 | 3.1.1 | 4.1 | 3.2 | 4.2.1 | ||||||||||||||||||
| Photos | Photo viewer | ||||||||||||||||||||||||||||
| Video viewer | 2.0 | 2.0 | |||||||||||||||||||||||||||
| Crop, red eye fix, auto enhance and photo rotate | N/A | 5.0 | N/A | 5.0 | N/A | 5.0 | |||||||||||||||||||||||
| Camera | Camera | 1.0 | 2.0 | 3.0 | 4.0 | N/A | 4.1 | N/A | 4.2.1 | ||||||||||||||||||||
| Camcorder | N/A | ||||||||||||||||||||||||||||
| Auto-focus | 3.0 | 4.0 | N/A | N/A | |||||||||||||||||||||||||
| HDR | N/A | 4.1 | |||||||||||||||||||||||||||
| Crop, red eye fix, auto enhance and photo rotate | 5.0 | 5.0 | 5.0 | ||||||||||||||||||||||||||
| Panorama | N/A | 6.0 | N/A | N/A | 8.0 | N/A | 8.0 | ||||||||||||||||||||||
| Take still photos while recording video | N/A | N/A | N/A | N/A | |||||||||||||||||||||||||
| Photo filters | 7.0 | 7.0 | |||||||||||||||||||||||||||
| Burst mode | N/A | 7.0 | N/A | ||||||||||||||||||||||||||
| FaceTime | Video calling over Wi-Fi | N/A | 4.0 | 5.0 | 6.0 | 7.0 | N/A | 4.1 | 6.0 | 4.2.1 | 5.1 | 6.0 | 7.0.3 | 8.1 | 6.0 | 7.0.3 | 8.1 | ||||||||||||
| Video calling over 3G/LTE (iPad requires a cellular network) | N/A | 6.0 | N/A | N/A | N/A | 6.0 | 6.0.1 | 6.0.1 | |||||||||||||||||||||
| FaceTime Audio | 7.0 | 7.0 | 7.0 | 7.0 | |||||||||||||||||||||||||
| Photo Booth | A camera application with added special effects | N/A | N/A | 4.2.1 | 5.1 | 6.0 | 6.0 | ||||||||||||||||||||||
| Stocks | Stocks provided byYahoo! Finance | 1.0 | 2.0 | 3.0 | 4.0 | 5.0 | 6.0 | 7.0 | 8.0 | 1.1.3 | 2.1.1 | 3.1.1 | 4.1 | 6.0 | N/A | N/A | |||||||||||||
| Stocks Widget for Notification Center | N/A | 5.0 | N/A | 5.0 | |||||||||||||||||||||||||
| Weather | Weather provided byThe Weather Channel | N/A | 8.0 | N/A | 8.0 | ||||||||||||||||||||||||
| Weather Widget forNotification Center | 5.0 | 5.0 | 6.0 | 7.0 | 8.0 | 5.0 | 6.0 | N/A | 7.0 | 7.0.3 | 8.1 | 7.0 | 7.0.3 | 8.1 | |||||||||||||||
| Notes | A simple note-taking program | 1.0 | 2.0 | 3.0 | 4.0 | 1.1.3 | 2.1.1 | 3.1.1 | 4.1 | 3.2 | 4.2.1 | 5.1 | 6.0 | 6.0 | |||||||||||||||
| Maps | Assisted GPS(iPad requires a cellular network) | N/A | N/A | 6.0.1 | 6.0.1 | ||||||||||||||||||||||||
| Apple-sourced maps | N/A | 6.0 | N/A | 6.0 | 6.0 | N/A | 6.0 | 6.0 | |||||||||||||||||||||
| Turn-by-turn navigationusing Apple-sourced maps | N/A | 6.0 | N/A | ||||||||||||||||||||||||||
| Reminders | A to-do list application | N/A | 5.0 | 5.0 | 5.0 | N/A | 5.0 | 5.0 | 5.1 | 6.0 | 6.0 | ||||||||||||||||||
| Location-based reminders (iPad requires a cellular network) | N/A | N/A | N/A | 6.0.1 | 6.0.1 | ||||||||||||||||||||||||
| Voice Memos | Voice recorder | 3.0 | 3.0 | 4.0 | 3.0 | 3.1.1 | 4.1 | 6.0 | N/A | N/A | |||||||||||||||||||
| Calculator | Calculator | 1.0 | 2.0 | 1.1 | 2.1.1 | ||||||||||||||||||||||||
| Scientific calculator (triggered by rotating to landscape) | 2.0 | 2.0 | |||||||||||||||||||||||||||
| Clock | World clock,stopwatch,alarm clockand timer | 1.0 | 1.1 | N/A | 6.0 | 7.0.3 | 8.1 | 6.0 | 7.0.3 | 8.1 | |||||||||||||||||||
| Settings | Settings | 3.2 | 4.2.1 | 5.1 | 6.0 | ||||||||||||||||||||||||
| Contacts | Standalone address/phone book | 2.0 | |||||||||||||||||||||||||||
| iTunes Store | Access to the iTunes Store and iTunes Podcast Directory | 1.1 | |||||||||||||||||||||||||||
| App Store | To buy or get iOS apps | 2.0 | 2.0 | ||||||||||||||||||||||||||
| Compass | Compass | N/A | N/A | N/A | N/A | ||||||||||||||||||||||||
| Game Center | Play multiplayer games with other users, track in-game achievements, view leaderboards. |
4.1 | 8.0 | N/A | 4.1 | 6.0 | 4.2.1 | 4.2.1 | 5.1 | 6.0 | 7.0.3 | 8.1 | 6.0 | 7.0.3 | 8.1 | ||||||||||||||
| Voice Control | Simple voice control (disabling Siri may be necessary) | 3.0 | 4.0 | N/A | 3.1.1 | 4.1 | N/A | N/A | |||||||||||||||||||||
| Siri | A personal voice assistant | N/A | N/A | N/A | 6.0 | 6.0 | 7.0.3 | 8.1 | 6.0 | 7.0.3 | 8.1 | ||||||||||||||||||
| Voice dictation | 5.1 | ||||||||||||||||||||||||||||
| Touch ID | A fingerprint recognitionfeature built into the home button; able to unlock the device and make iTunes/App Store purchases |
N/A | 7.0 | N/A | N/A | N/A | |||||||||||||||||||||||
| Wallet | A virtual wallet application for passes, tickets, coupons and loyalty cards (called Passbook prior to iOS 9) | N/A | 6.0 | 7.0 | N/A | 6.0 | N/A | N/A | |||||||||||||||||||||
| CarPlay | A new in-vehicle extended iOS functionality | N/A | 7.1.1 | N/A | |||||||||||||||||||||||||
| AirDrop | An ad-hoc Wi-Fi/Bluetooth-based file sharing mechanism | N/A | 7.0 | N/A | 7.0 | N/A | 7.0 | 8.1 | 7.0 | 8.1 | |||||||||||||||||||
| Health | An app that monitors and analyzes an individual’s biochemistry and physiology | N/A | 8.0 | N/A | 8.0 | N/A | N/A | ||||||||||||||||||||||
| Tips | An app that gives tutorials for various functions | N/A | 8.0 | 8.0 | |||||||||||||||||||||||||
| Podcasts | Integrated podcast player | ||||||||||||||||||||||||||||
| iBooks | Integrated e-book viewer | ||||||||||||||||||||||||||||
| News | N/A | 9.0 | N/A | 9.0 | N/A | 9.0 | 9.0 | ||||||||||||||||||||||
| Find My iPhone | |||||||||||||||||||||||||||||
| Find My Friends | |||||||||||||||||||||||||||||
| iCloud Drive | (turned off by default – can be enabled in Settings) | ||||||||||||||||||||||||||||
| Series | iPhone | iPod Touch | iPad | iPad Mini | Final supported iOS version |
|||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Model | 1st | 3G | 3GS | 4 | 4S | 5 | 5C | 5S | 6 | 6 Plus | 1st | 2nd | 3rd | 4th | 5th | 6th | 1st | 2 | 3rd | 4th | Air | Air 2 | 1st | 2 | 3 | |||||||
| iPod | iPhone media player, iPad music player | 1.0 | 2.0 | 3.0 | 4.0 | N/A | N/A | 3.2 | 4.2.1 | N/A | N/A | 4.2.10(CDMA) 4.3.5 |
||||||||||||||||||||
| YouTube | YouTubevideo streamer | 5.0 | N/A | 1.1 | 2.1.1 | 3.1.1 | 4.1 | N/A | 5.1 | N/A | 5.1.1 | |||||||||||||||||||||
| Maps | Google Maps withGoogle Street View | 1.1.3 | ||||||||||||||||||||||||||||||
| Weather | Weather provided by Yahoo!Weather | 6.0 | 7.0 | N/A | 6.0 | N/A | N/A | 7.1.2 | ||||||||||||||||||||||||
| Nike + iPod | Records the distance and pace of a walk or run; can connect to Nike + iPod sensor (turned off by default – can be enabled in Settings) | N/A | N/A | 8.4.1 | ||||||||||||||||||||||||||||
| Newsstand | A newspaper and magazine store | N/A | 8.0 | N/A | 5.0 | 8.4 | N/A | 5.1 | 6.0 | 7.0.3 | 8.1 | 6.0 | 7.0.3 | 8.1 | ||||||||||||||||||
On the iPhone and iPod Touch, apps such as Voice Memos, Contacts, Calculator, and Compass are in one folder called “Utilities” in iOS 4 and above.[42][43] Many of the included applications are designed to share data (e.g., a phone number can be selected from an email and saved as a contact or dialed for a phone call). For the iOS 7 update, the folder name was changed to “Extras”.
The Messages app supports Apple’s iMessage service in iOS 5 or above; iMessage supports sending free text or multimedia messages to other iOS devices running iOS 5 and above (similar to BlackBerry Messenger), and to Macs running OS X Mavericks.
Panoramic photography is available only on iPhone 4S and later models, and the fifth generation iPod Touch.[44][45]
The bottom row of applications, called the dock, is used to delineate the iPhone’s main purposes: originally Phone, Mail, Safari, iPod. Starting with iOS 5, the iPod app was split into two apps, Music and Videos, as it always has been on the iPod Touch, and the Music app replaced the iPod app in the dock.
Since the inception of the iPhone, various apps were either integrated into iOS (e.g. Podcasts, iBooks, Siri, Facebook, Twitter) or disintegrated (e.g. Podcasts, iTunes U, YouTube). In iOS 6, the previously integrated YouTube app was removed from the software, and moved to the App Store. The Podcasts and iTunes U features (previously integrated in the Music and Videos apps) also became their own apps in the App Store. In iOS 7, the iPhone gains a dedicated FaceTime app (previously integrated into the Phone app), as it had been on the iPod Touch and iPad since iOS 4. In iOS 8, the iBook and Podcast apps became integrated into iOS, though the App Store app is still available for download. In iOS 9, the Find My iPhone and Find My Friends became integrated into iOS; App Store versions are unavailable for download.
Starting January 2008, the iPod Touch retains the same applications that are present by default on the iPhone, with the exception of the Phone and Compass (and also previously, Messages before iOS 5 and Camera before the fourth-generation iPod Touch) apps. The original dock layout was Music, Videos, Photos, and iTunes. In iPhone OS 3, the layout was changed to Music, Videos, Safari, and App Store. For the fourth-generation iPod Touch, it includes FaceTime and Camera, and the dock layout had changed to Music, Mail, Safari, Videos, with the release of iOS 4. With the release of the new fifth-generation iPod Touch and iOS 6, the dock layout was changed to Messages, Mail, Safari, Music, similar to the iPhone.
The iPad and iPad Mini come with the same applications as the iPod Touch, excluding Stocks, Weather, Calculator, and the Nike + iPod app (and also previously, Clock before iOS 6). Additionally, starting with the iPad 2, they have the unique Photo Booth app. Most of the default applications, such as Safari and Mail, are completely rewritten to take advantage of the iPad’s and iPad Mini’s larger displays. The original dock layout was Safari, Mail, Photos, iPod. Separate music and video apps are provided, as on the iPod Touch, although (as on the iPhone) the music app was named “iPod”. In iOS 5, it was changed to “Music” and the dock layout became Safari, Mail, Photos, Music. In iOS 6, Videos replaced Photos in the dock. In iOS 7, the default dock layout was changed to match that of the iPod Touch.
Multitasking
Multitasking for iOS was first released in June 2010 along with the release of iOS 4.0.[46][47] Only certain devices—iPhone 4, iPhone 3GS, and iPod Touch 3rd generation—were able to use multitasking.[48] The iPad did not get multitasking until the release of iOS 4.2.1 in November 2010.[49] Currently, multitasking is supported on iPhone 3GS or newer, iPod Touch 3rd generation or newer, and all iPad models.[50]
Implementation of multitasking in iOS has been criticized for its approach, which limits the work that applications in the background can perform to a limited function set and requires application developers to add explicit support for it.[48][51]
Before iOS 4, multitasking was limited to a selection of the applications Apple included on the device. Users could, however “jailbreak” their device in order to unofficially multitask.[52] Starting with iOS 4, on third-generation and newer iOS devices, multitasking is supported through seven background APIs:[53]
- Background audio – application continues to run in the background as long as it is playing audio or video content[54]
- Voice over IP – application is suspended when a phone call is not in progress[54]
- Background location – application is notified of location changes[54]
- Push notifications
- Local notifications – application schedules local notifications to be delivered at a predetermined time[54]
- Task completion – application asks the system for extra time to complete a given task[54]
- Fast app switching – application does not execute any code and may be removed from memory at any time[54]
In iOS 5, three new background APIs were introduced:
- Newsstand – application can download content in the background to be ready for the user[54]
- External Accessory – application communicates with an external accessory and shares data at regular intervals[54]
- Bluetooth Accessory – application communicates with a bluetooth accessory and shares data at regular intervals[54]
In iOS 7, Apple introduced a new multitasking feature, providing all apps with the ability to perform background updates. This feature prefers to update the user’s most frequently used apps and prefers to use WiFi networks over a cellular network, without markedly reducing the device’s battery life.
Switching applications
In iOS 4.0 to iOS 6.x, double-clicking the home button activates the application switcher. A scrollable dock-like interface appears from the bottom, moving the contents of the screen up. Choosing an icon switches to an application. To the far left are icons which function as music controls, a rotation lock, and on iOS 4.2 and above, a volume controller.
With the introduction of iOS 7, double clicking the home button also activates the application switcher. However, unlike previous versions it displays screenshots of open applications on top of the icon and horizontal scrolling allows for browsing through previous apps, and it is possible to close applications by dragging them up, similar to howWebOS handled multiple cards.[55]
With the introduction of iOS 9, the application switcher received a significant visual change; whilst still retaining the card metaphor introduced in iOS 7, the application icon is smaller, and appears above the screenshot (which is now larger, due to the removal of “Recent and Favorite Contacts”), and each application “card” overlaps the other, forming arolodex effect as the user scrolls. Now, instead of the home screen appearing at the leftmost of the application switcher, it appears rightmost.[56]
Ending tasks
In iOS 4.0 to iOS 6.x, briefly holding the icons in the application switcher makes them “jiggle” (similarly to the homescreen) and allows the user to force quit the applications by tapping the red minus circle that appears at the corner of the app’s icon.[57] Clearing applications from multitasking stayed the same from iOS 4.0 through 6.1.6, the last version of iOS 6.
As of iOS 7, the process has become faster and easier. In iOS 7, instead of holding the icons to close them, they are closed by simply swiping them upwards off the screen. Up to three apps can be cleared at a time compared to one in versions up to iOS 6.1.6.[58]
Task completion
Task completion allows apps to continue a certain task after the app has been suspended.[59][60] As of iOS 4.0, apps can request up to ten minutes to complete a task in the background.[61] This doesn’t extend to background up- and downloads though (e.g. if you start a download in one application, it won’t finish if you switch away from the application).
Siri
Siri is a personal assistant and knowledge navigator which works as an application on supported devices. The service, directed by the user’s spoken commands, can do a variety of different tasks, such as call or text someone, open an app, search the web, lookup sports information, find directions or locations, and answer general knowledge questions (e.g. “How many cups are in a gallon?”).[62] Siri was updated in iOS 7 with a new interface, faster answers, Wikipedia, Twitter, and Bing support and the voice was changed to sound more human. Siri is currently only available on the iPhone 4S and later iPhones, the fifth and sixth generation iPod Touch, all of the models of the iPad Mini, and the third-generation and later iPads.
Game Center
Game Center is an online multiplayer “social gaming network”[63] released by Apple.[64] It allows users to “invite friends to play a game, start a multiplayer game through matchmaking, track their achievements, and compare their high scores on a leaderboard.” iOS 5 and above adds support for profile photos.[63]
Game Center was announced during an iOS 4 preview event hosted by Apple on April 8, 2010. A preview was released to registered Apple developers in August.[63] It was released on September 8, 2010 with iOS 4.1 on iPhone 4, iPhone 3GS, and iPod Touch 2nd generation through 4th generation.[65] Game Center made its public debut on the iPad with iOS 4.2.1.[66] There is no support for the iPhone 3G, original iPhone and the first-generation iPod Touch (the latter two devices did not have Game Center because they did not get iOS 4). However, Game Center is unofficially available on the iPhone 3G via a hack.[67]
Development
Authorized third-party native applications are available through Apple’s App Store for devices running iPhone OS 2.0 and higher. Native apps must be written in Swift or Objective-C (with some elements optionally in C or C++) and compiled specifically for iOS and the 64-bit ARM architecture or previous 32-bit one (typically using Xcode). Third-party attemptshave been made to allow apps written with Java, .NET, and Adobe Flash to run on iOS devices, but due to Apple restrictions these are generally not available in the iOS App Store.
The Safari web browser supports web applications as with other web browsers. Hybrid apps embed a mobile web site inside a native app, possibly using a hybrid framework likeApache Cordova or React Native.
SDK
On October 17, 2007, in an open letter posted to Apple’s “Hot News” weblog, Steve Jobs announced that a software development kit (SDK) would be made available to third-party developers in February 2008.[68] The SDK was released on March 6, 2008, and allows developers to make applications for the iPhone and iPod Touch, as well as test them in an “iPhone simulator”. However, loading an application onto the devices is only possible after paying an iPhone Developer Program fee.
The fees to join the respective developer programs for iOS and OS X were each set at US$99.00 per year. As of July 20, 2011, Apple released Xcode on its Mac App Store free to download for all OS X Lion users, instead of as a standalone download. Users can create and develop iOS and OS X applications using a free copy of Xcode; however, they cannot test their applications on a physical iOS device, or publish them to the App store, without first paying the yearly $99.00 iPhone Developer or Mac Developer Program fee.[69]
Since the release of Xcode 3.1, Xcode is the development environment for the iOS SDK.
Developers are able to set any price above a set minimum for their applications to be distributed through the App Store, keeping 70% for the developer, and leaving 30% for Apple. Alternatively, they may opt to release the application for free and need not pay any costs to release or distribute the application except for the membership fee.[70]
iOS is the second most popular mobile operating system platform in the world by sales, after Android.
By the middle of 2012, there were 410 million devices activated.[71] At WWDC 2014, Tim Cook said 800 million devices had been sold by June 2014.[72]
During Apple’s quarterly earnings call in January 27, 2015, Apple announced that they have now sold one billion iOS devices since 2007[73] (a little less than Android sold in 2014 only[74]).
Jailbreaking
Since its initial release, iOS has been subject to a variety of different hacks centered around adding functionality not allowed by Apple.[75] Prior to the 2008 debut of Apple’s nativeiOS App Store, the primary motive for jailbreaking was to bypass Apple’s purchase mechanism for installing the App Store’s native applications.[76] Apple claimed that it will not release iOS software updates designed specifically to break these tools (other than applications that perform SIM unlocking); however, with each subsequent iOS update, previously un-patched jailbreak exploits are usually patched.[77]
Since the arrival of Apple’s native iOS App Store, and—along with it—third-party applications, the general motives for jailbreaking have changed.[78] People jailbreak for many different reasons, including gaining filesystem access, installing custom device themes, and modifying the device SpringBoard. An additional motivation is that it may enable the installation of pirated apps. On some devices, jailbreaking also makes it possible to install alternative operating systems, such as Android and the Linux kernel. Primarily, users jailbreak their devices because of the limitations of iOS. Depending on the method used, the effects of jailbreaking may be permanent or temporary.[79]
In 2010, the Electronic Frontier Foundation (EFF) successfully convinced the U.S. Copyright Office to allow an exemption to the general prohibition on circumvention of copyright protection systems under the Digital Millennium Copyright Act (DMCA). The exemption allows jailbreaking of iPhones for the sole purpose of allowing legally obtained applications to be added to the iPhone.[80] The exemption does not affect the contractual relations between Apple and an iPhone owner, for example, jailbreaking voiding the iPhone warranty; however, it is solely based on Apple’s discretion on whether they will fix jailbroken devices in the event that they need to be repaired. At the same time, the Copyright Office exempted unlocking an iPhone from DMCA’s anticircumvention prohibitions.[81] Unlocking an iPhone allows the iPhone to be used with any wireless carrier using the same GSM or CDMA technology for which the particular phone model was designed to operate.[82]
Unlocking
Initially most wireless carriers in the US did not allow iPhone owners to unlock an iPhone for use with other carriers. However AT&T Mobility allowed iPhone owners who have satisfied the requirements of their contract to unlock their iPhone.[83] Instructions to unlock the device are available from Apple,[84] but it is ultimately the sole discretion of the carrier to authorize the device to be unlocked.[85] This allows the use of a carrier sourced iPhone on other networks. However, because T-Mobile primarily uses a different band than AT&T for its 3G data signals, the iPhone will only work at 3G speeds on the T-Mobile 1900 MHz network.[86] There are programs to break these restrictions, but are not supported by Apple and most often not a permanent unlock, known as soft-unlock.[87]
Digital rights management
The closed and proprietary nature of iOS has garnered criticism, particularly by digital rights advocates such as the Electronic Frontier Foundation, computer engineer and activistBrewster Kahle, Internet-law specialist Jonathan Zittrain, and the Free Software Foundation who protested the iPad’s introductory event and have targeted the iPad with their “Defective by Design” campaign.[88][89][90][91] Competitor Microsoft, via a PR spokesman, criticized Apple’s control over its platform.[92]
At issue are restrictions imposed by the design of iOS, namely digital rights management (DRM) intended to lock purchased media to Apple’s platform, the development model (requiring a yearly subscription to distribute apps developed for the iOS), the centralized approval process for apps, as well as Apple’s general control and lockdown of the platform itself. Particularly at issue is the ability for Apple to remotely disable or delete apps at will.
Some in the tech community have expressed concern that the locked-down iOS represents a growing trend in Apple’s approach to computing, particularly Apple’s shift away from machines that hobbyists can “tinker with” and note the potential for such restrictions to stifle software innovation.[93][94] Former Facebook developer Joe Hewitt protested against Apple’s control over its hardware as a “horrible precedent” but praised iOS’s sandboxing of apps.[95]
Kernel
The iOS kernel is XNU, the kernel of Darwin. The original iPhone OS (1.0) up to iPhone OS 3.1.3 used Darwin 9.0.0d1. iOS 4 was based on Darwin 10. iOS 5 was based on Darwin 11. iOS 6 was based on Darwin 13. iOS 7 and iOS 8 are based on Darwin 14. iOS 9 is based on Darwin 15.[96]
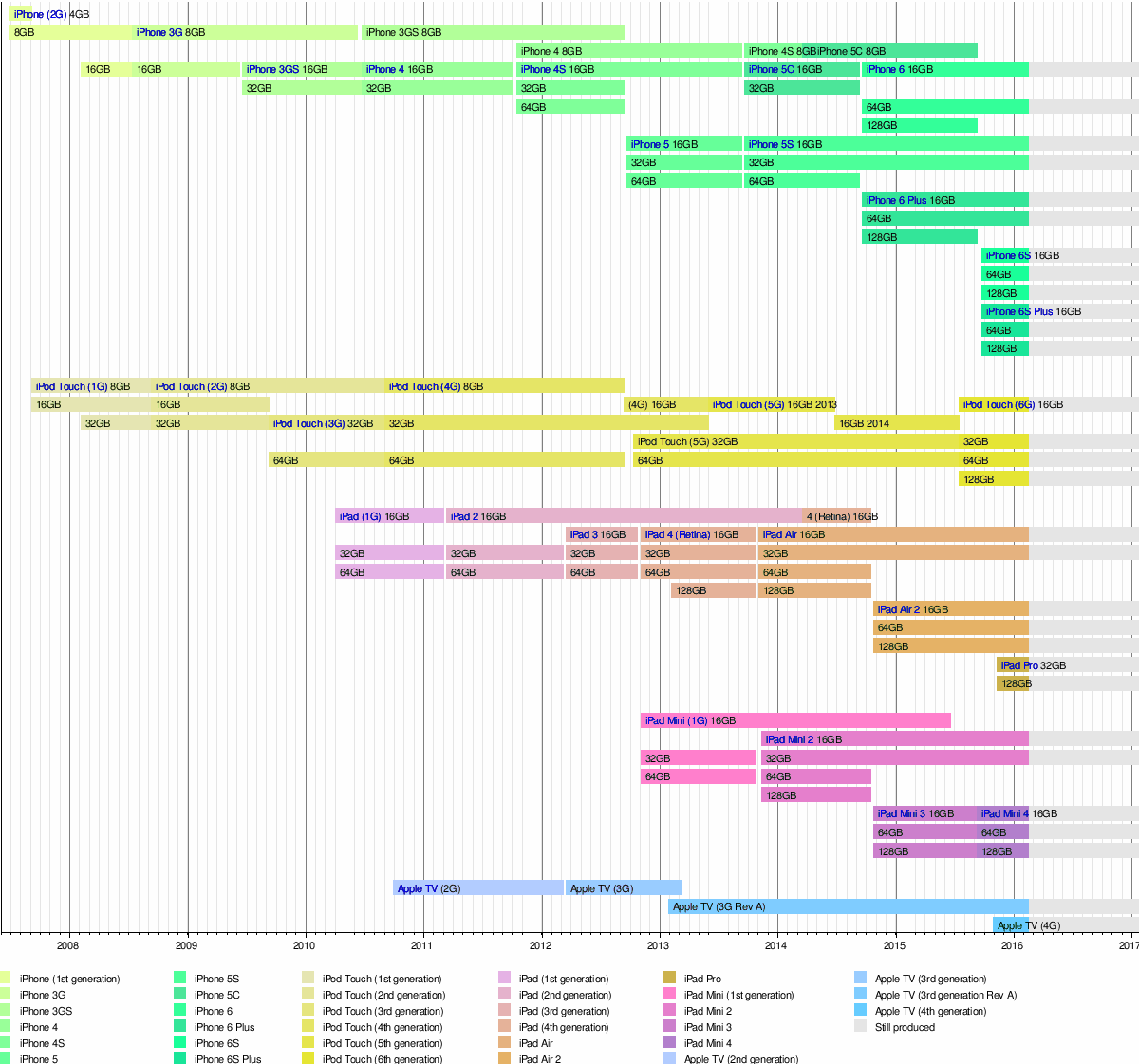
Devices
See also
References
- Jump up^ “Apple security updates”. Apple. 2016-01-19. Retrieved 2016-01-19.
- Jump up^ “About the security content of Apple TV 7.2”. Apple. 2015-04-08. Retrieved2015-04-08.
- Jump up^ “About the security content of tvOS 9.1”. Apple. 2015-12-08. Retrieved 2015-12-09.
- Jump up^ “Apple – iPad Pro – Specs”. Apple. Retrieved October 24, 2015.
- Jump up^ “Apple – iPad mini 4 – Specs”. Apple. Retrieved October 24, 2015.
- Jump up^ “Apple – iPad Air 2 – Technical Specifications”. Apple. Retrieved October 24, 2015.
- Jump up^ “Apple – iPhone 6s – Technical Specifications”. Apple. Retrieved October 24, 2015.
- Jump up^ Steve Ranger (January 16, 2015). “iOS versus Android. Apple App Store versus Google Play: Here comes the next battle in the app wars”. ZDNet.
- Jump up^ Nathan Ingraham (June 8, 2015). “Apple’s App Store has passed 100 billion app downloads”. The Verge.
- Jump up^ Cunningham, Andrew (September 16, 2015). “iOS 9, thoroughly reviewed | Ars Technica”. Ars Technica. Retrieved September 17, 2015.
- Jump up^ Siracusa, John. “Can’t Help Falling in Love”. Ars Technica. Conde Nast. Retrieved5 September 2014.
- Jump up^ Satariano, Adam; Peter Burrows; Brad Stone (2011-12-01). “Scott Forstall, the Sorcerer’s Apprentice at Apple”. Businessweek. Retrieved 2011-10-13.
- Jump up^ Viticci, Federico (2012-10-29). “Major Changes at Apple: Scott Forstall Leaving, Jony Ive To Lead Human Interface Across Company”. Macstories.net. Retrieved 2012-12-06.
- Jump up^ Honan, Matthew (January 9, 2007). “Apple unveils iPhone”. Macworld. RetrievedJanuary 16, 2010.
- Jump up^ “What operating system does the iPhone use? Can it run MacOS X applications like Skype and Photoshop?”. July 5, 2010. Retrieved April 4, 2014.
- Jump up^ “Apple – iPhone – Features – OS X”. Archived from the original on January 11, 2008. Retrieved June 15, 2010.
- Jump up^ Gonsalves, Antone (October 11, 2007). “Apple Launches iPhone Web Apps Directory”. InformationWeek. Retrieved February 16, 2010.
- Jump up^ Ziegler, Chris (June 11, 2007). “Apple announces third-party software details for iPhone”. Engadget. Retrieved June 9, 2010.
- Jump up^ Nik Fletcher (October 17, 2007). “Apple: “we plan to have an iPhone SDK in developers’ hands in February””. TUAW – The Unofficial Apple Weblog. RetrievedJune 8, 2010.
- Jump up^ “Apple Reports Fourth Quarter Results”. Apple Inc. October 22, 2007. RetrievedJune 9, 2010.
- Jump up^ “Apple Launches iPhone Web Apps Directory”. Apple. January 27, 2010. RetrievedMay 8, 2010.
- Jump up^ Tartakoff, Joseph (June 7, 2010). “Apple Avoids iPhone-Like Trademark Battle Thanks To Cisco, FaceTime Deals”. paidContent. Retrieved February 2, 2011.
- Jump up^ Saylor, Michael (2012). The Mobile Wave: How Mobile Intelligence Will Change Everything. Vanguard Press. p. 33. ISBN 1-59315-720-7.
- Jump up^ “Android and iOS Squeeze the Competition, Swelling to 96.3% of the Smartphone Operating System Market for Both 4Q14 and CY14, According to IDC” (Press release). IDC. February 24, 2015.
- Jump up^ “Worldwide Tablet Growth Hits the Brakes, Slowing to the Low Single Digits in the Years Ahead, According to IDC” (Press release). IDC. March 12, 2015.
- Jump up^ “StatCounter Global Stats: Top 7 Mobile Operating Systems on Feb 2015”. Retrieved6 March 2015.
- Jump up^ Why Do iPod touch Software Updates Cost Money?. Ipod.about.com (September 9, 2009). Retrieved on July 30, 2013.
- Jump up^ Truta, Filip (June 15, 2010). “iOS 4 Software Update for iPod touch Is Free”.Softpedia. Retrieved June 7, 2014.
- Jump up^ “http://help.apple.com/iphone/8/#/iph3bd00bbb”. help.apple.com. Retrieved2015-05-24. External link in
|title=(help) - Jump up^ “About iOS passcodes – Apple Support”. support.apple.com. Retrieved 2015-05-24.
- Jump up^ “Apple’s iOS 7 brings quick Spotlight search access to every app page”.AppleInsider. June 10, 2013. Retrieved September 18, 2013.
- Jump up^ “Search on iPad with iOS 7”. October 21, 2013. Retrieved March 1, 2014.
- Jump up^ “Hands-on with the new, proactive Spotlight in iOS 9”. September 16, 2015. Retrieved October 17, 2015.
- Jump up^ Matthias Böhmer, Antonio Krüger. A Study on Icon Arrangement by Smartphone Users. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems (CHI ’13). ACM, New York, NY, USA, 2137–2146.
- Jump up^ Gruber, John. “4”. Daring Fireball. Retrieved 11 July 2015.
- Jump up^ “Fonts – Apple Developer”. developer.apple.com. Retrieved 2015-09-08.
- Jump up^ “iOS: Using Newsstand”. Apple Inc. Retrieved September 29, 2012.
- Jump up^ “How to create nested folders on iOS 7”. Retrieved December 20, 2013.
- Jump up^ “iPhone 4S – Always know what’s up in Notification Center”. Apple Inc. RetrievedAugust 13, 2012.
- Jump up^ “iOS: A wide range of features for a wide range of needs.”. Apple Inc. RetrievedJune 12, 2015.
- Jump up^ “iOS: Understanding Restrictions”. Apple Inc. Retrieved September 29, 2012.
- Jump up^ “iPhone Applications”. Apple Inc. July 10, 2008. Retrieved July 11, 2008.
- Jump up^ “iOS 3.1 Software Update”. Apple Inc.
- Jump up^ “How to take a panoramic photo with iOS 6”. CNET. CBS Interactive.
- Jump up^ “Mastering panoramic photography in iOS 6”. CNET. CBS Interactive.
- Jump up^ “iOS 4 iPhone Update RELEASED: A Guide To iOS 4”. The Huffington Post. June 21, 2010. Retrieved April 13, 2013.
- Jump up^ Albanesius, Chloe (June 21, 2010). “Apple iPhone iOS 4 Software Update Expected Monday”. PC Magazine. Retrieved April 14, 2013.
- ^ Jump up to:a b Cheng, Jacqui (June 21, 2010). “Ars reviews iOS 4: what’s new, notable, and what needs work”. Ars Technica. Retrieved April 14, 2013.
- Jump up^ Ray, Bill (November 22, 2010). “iOS 4.2 multi-tasking comes to the iPad”. The Register. Retrieved April 14, 2013.
- Jump up^ “iOS: Understanding multitasking”. Apple. Retrieved 2013-09-14.
- Jump up^ Newman, Jared (June 22, 2010). “Multitasking With iOS 4 is Horrible: Apple Blew It”. PC World. Retrieved April 14, 2013.
- Jump up^ “iOS 4 walkthrough”. June 14, 2010. Retrieved June 14, 2010.
- Jump up^ “Apple announces multitasking for iPhone OS 4 (iPhone 3GS/iPod touch G3 only)”. April 8, 2010. Retrieved June 14, 2010.
- ^ Jump up to:a b c d e f g h i “iOS Application Programming Guide – Background Execution”. Developer.apple.com. Retrieved September 4, 2015.
- Jump up^ “Jon Rubinstein: OS X and iOS 7 borrow features from webOS”. RetrievedSeptember 23, 2013.
- Jump up^ Prabhu, Gautam. “iOS 9 vs. iOS 8: A look at the UI changes in iOS 9”. iPhone Hacks. Retrieved 20 September 2015.
- Jump up^ “iOS: Force an app to close”. Apple Inc. Retrieved October 9, 2012.
- Jump up^ “iOS 7 multitasking”. Tuaw. September 18, 2013. Retrieved March 21, 2014.
- Jump up^ Snell, Jason (April 8, 2010). “Inside iPhone 4.0’s multitasking”. Macworld. RetrievedApril 14, 2013.
- Jump up^ “Apple iPhone 4”. CNET. June 23, 2010. Retrieved April 14, 2013.
- Jump up^ Hollington, Jesse (June 21, 2010). “Instant Expert: Secrets & Features of iOS 4”. iLounge. Retrieved April 14, 2013.
- Jump up^ “iOS 6 — Ask Siri to help you get things done”. Apple. Retrieved February 18, 2013.
- ^ Jump up to:a b c “What’s New in iOS 4”. Apple. Retrieved June 14, 2010.
- Jump up^ “Apple’s Game Center debuts next week – Game Hunters: In search of video games and interactive awesomeness”. USA Today. January 9, 2010. Retrieved September 1,2010.
- Jump up^ Holt, Chris. “iOS 4.1’s GameCenter to Hit iPhone Next Week – PCWorld Business Center”. Pcworld.com. Retrieved September 1, 2010.
- Jump up^ “iOS 4.2 Software Update for iPad”. Apple Inc. Retrieved October 9, 2012.
- Jump up^ “Game Center”. Apple. Sep 2010. Retrieved September 7, 2010.
- Jump up^ Jobs, Steve (October 17, 2007). “Third Party Applications on the iPhone”. Apple Inc.
- Jump up^ “Which Developer Program is for you?”. September 2012. Retrieved June 14, 2013.
- Jump up^ “Introducing the iPhone Developer Program”. Apple Inc. Retrieved June 14, 2013.
- Jump up^ “iOS leapfrogs Android with 410 million devices sold and 650,000 apps”. InsideMobileApps. July 24, 2012. Retrieved July 24, 2012.
- Jump up^ “Apple has sold more than 800 million iOS devices, 130 million new iOS users in the last year”. Retrieved June 2, 2014.
- Jump up^ “Apple has sold one billion iOS devices, company claims”. Retrieved April 15, 2015.
- Jump up^ Brad Reed. “Android device sales 2014: 1.1 billion – BGR”. BGR.
- Jump up^ Ricker, Thomas (July 10, 2007). “iPhone Hackers: “we have owned the filesystem””.Engadget. Retrieved October 16, 2015.
- Jump up^ Healey, Jon (August 6, 2007). “Hacking the iPhone”. Los Angeles Times. RetrievedAugust 6, 2007.
- Jump up^ “Apple’s Joswiak: We Don’t Hate iPhone Coders”. September 11, 2007. RetrievedJune 9, 2010.
- Jump up^ Baig, Edward C. (June 26, 2007). “Apple’s iPhone isn’t perfect, but it’s worthy of the hype”. USA Today. Retrieved June 28, 2007.
- Jump up^ IPad, MAX (May 6, 2010). “Jailbreaking Explained”. IPad Forums. RetrievedNovember 4, 2012.
- Jump up^ Kravets, David (July 26, 2010). “U.S. Declares iPhone Jailbreaking Legal, Over Apple’s Objections”. Wired. Retrieved December 13, 2011.
- Jump up^ “U.S. Copyright Office Final 2010 Anti-Circumvention Rulemaking” (PDF). U.S. Copyright Office. July 27, 2010. Retrieved August 21, 2012.
- Jump up^ Mobile, Know Your (May 19, 2010). “Locked / Unlocked – a definition of the terms Locked and Unlocked from the Know Your Mobile mobile phone glossary”. Know Your Mobile. Retrieved November 4, 2012.
- Jump up^ “AT&T – What are the eligibility requirements for unlocking iPhone?”. AT&T. Retrieved August 21, 2012.
- Jump up^ “iPhone: About unlocking”. Apple Inc. Website. May 22, 2012. Retrieved August 21,2012.
- Jump up^ “iPhone: Wireless Carrier Support and Features”. Apple Inc. Website. April 12, 2013. Retrieved May 13, 2013.
- Jump up^ “How to unlock your AT&T iPhone”. USA Today. April 9, 2012. Retrieved August 21,2012.
- Jump up^ “Unauthorized modification of iOS can cause security vulnerabilities, instability, shortened battery life, and other issues”. Apple Inc. Website. February 9, 2013. Retrieved May 13, 2013.
- Jump up^ “iPad DRM endangers our rights”.
- Jump up^ Anderson, Nate (January 27, 2010). “Protestors: iPad is nothing more than a golden calf of DRM”. Retrieved June 9, 2010.
- Jump up^ “Mobile Devices and the Next Computing Revolution”. February 3, 2010. RetrievedJune 9, 2010.
- Jump up^ Bobbie Johnson (February 1, 2010). “Apple iPad will choke innovation, say open internet advocates”. The Guardian. Retrieved February 7, 2010.
- Jump up^ “Microsoft PR spokesman condemns iPad for being “locked down””.
- Jump up^ “Apple’s Trend Away From Tinkering”. Slashdot. January 31, 2010. Retrieved June 9,2010.
- Jump up^ Steve Wozniak (Interviewee) (January 22, 2011). Campus Party Brasil 2011 – Geek Pride e Wozniak. Fragoso, Victor. Retrieved March 7, 2011.
- Jump up^ Leander Kahney (January 30, 2010). “Pundits On The iPad’s Closed System: It’s Doom For PCs, No It’s Great”. Retrieved June 9, 2010.
- Jump up^ Available in iOS 5 to iOS 7 via General > About > Diagnostics & Usage > Diagnostics & Usage Data >(date and time).panic.plist, after a kernel crash
Available in iOS 8 and iOS 9 via Privacy > Diagnostics & Usage > Diagnostics & Usage Data > JetsamEvent-(date and time).ips, when low in memory - Jump up^ Apple Inc., Apple press release library, Retrieved September 19, 2007.
- Jump up^ Mactracker (mactracker.ca), Apple Inc. model database, version as of 26 July 2007.
Further reading
- Hillegass, Aaron; Conway, Jon (March 22, 2012). iOS Programming: The Big Nerd Ranch Guide (3rd ed.). Pearson. p. 590. ISBN 978-0-321-82152-2.
- Turner, Kirby (December 19, 2011). Learning iPad Programming: A Hands-on Guide to Building iPad Apps with iOS 5 (1st ed.). Pearson. p. 816. ISBN 978-0-321-75040-2.
- Mark, Dave; LaMarche, Jeff (July 21, 2009). Beginning iPhone 3 Development: Exploring the iPhone SDK (1st ed.). Apress. p. 584. ISBN 1-4302-2459-2.
- Mark, Dave; LaMarche, Jeff (December 29, 2009). More iPhone 3 Development: Tackling iPhone SDK 3 (1st ed.). Apress. p. 552. ISBN 1-4302-2505-X.